
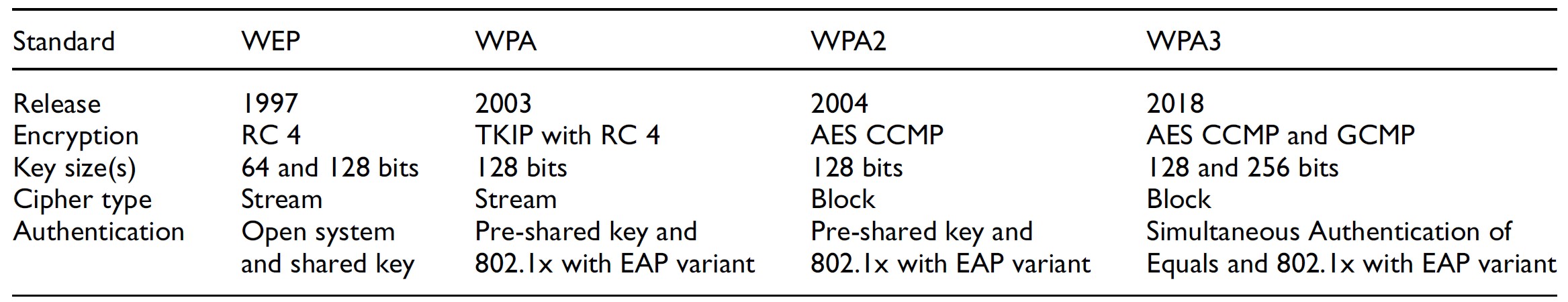
wifi - How long would it take to brute force an 11 character single-case alphanumeric password? - Information Security Stack Exchange

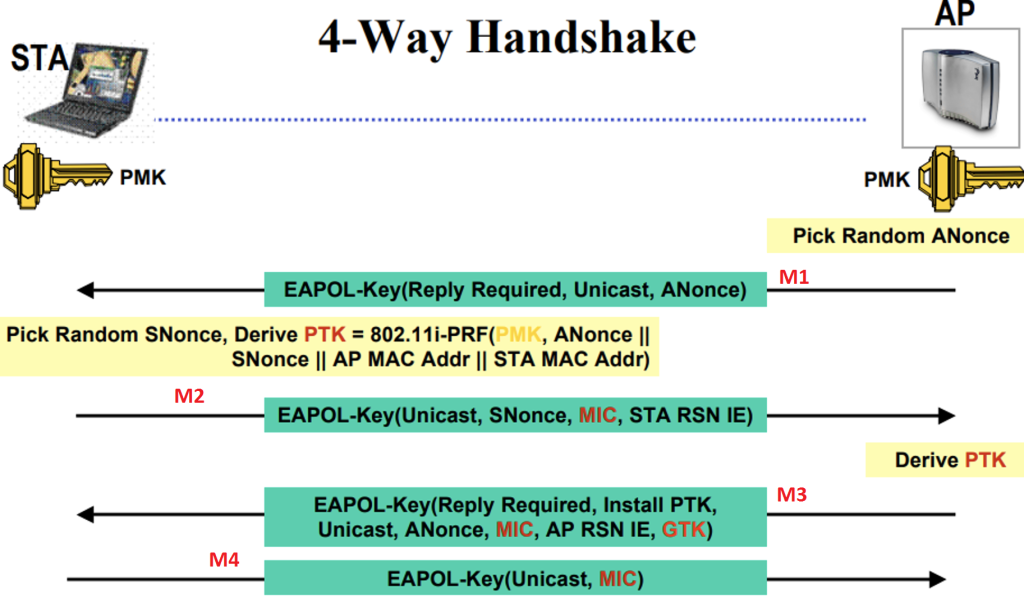
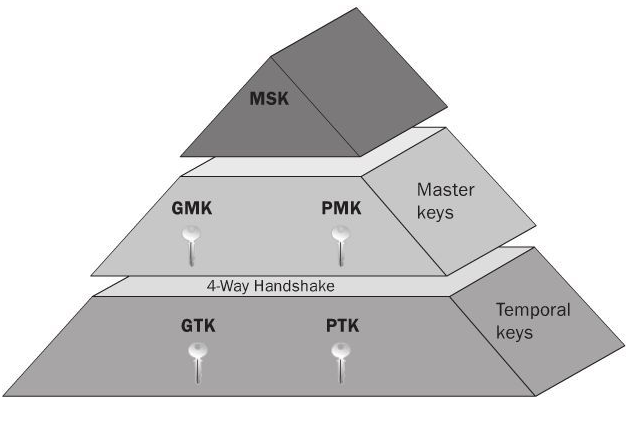
WPA-2 encryption and integrity check Message integrity check (MIC): AES... | Download Scientific Diagram

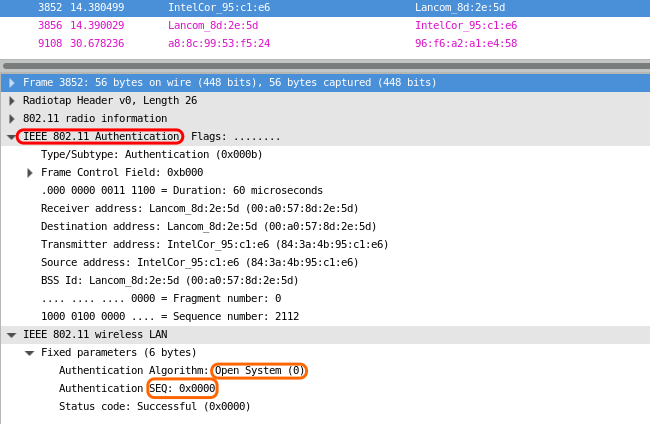
encryption - How is TSC (TKIP sequence counter) calculated, in WPA? - Information Security Stack Exchange

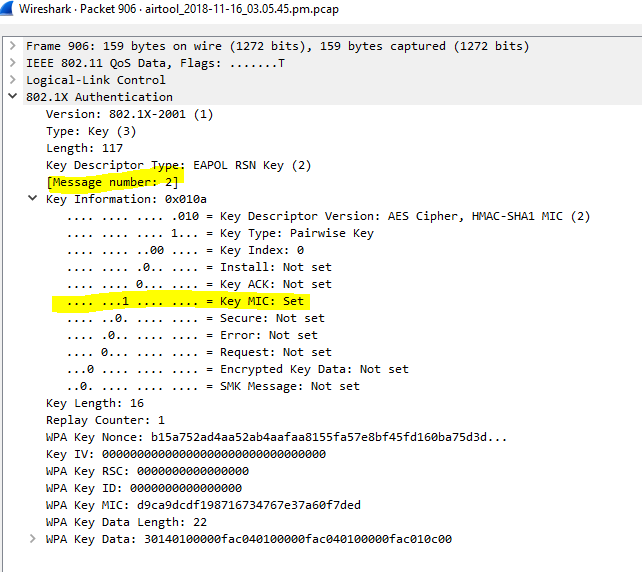


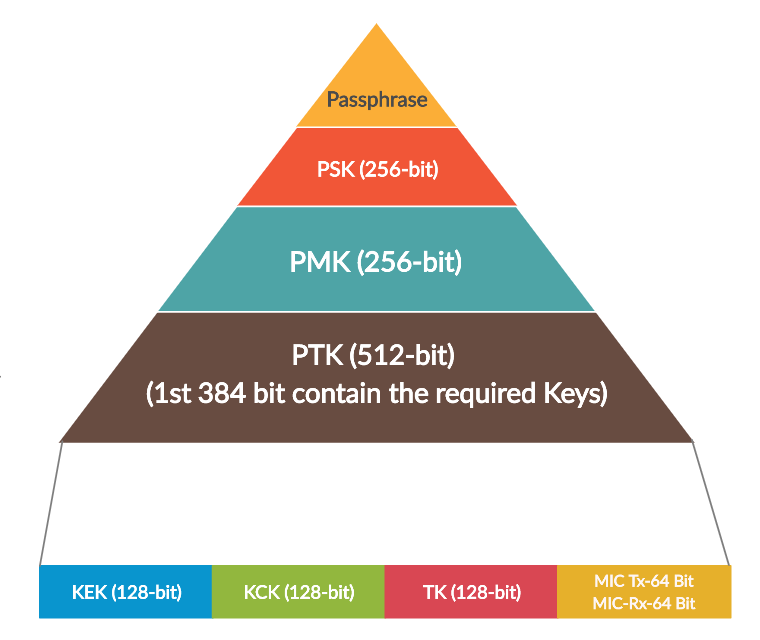
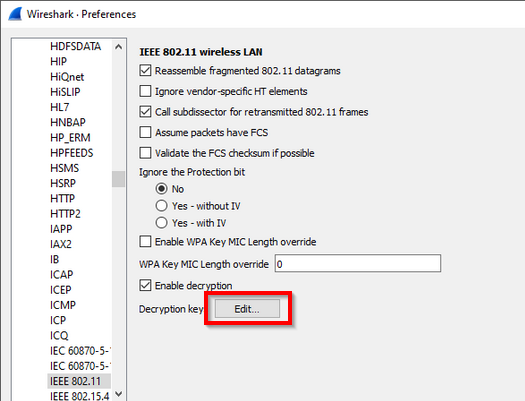


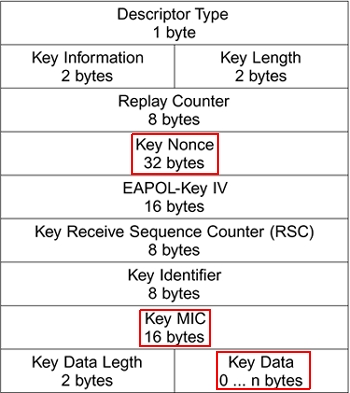

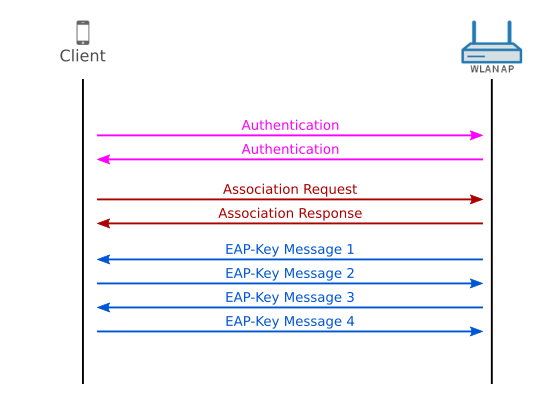
![Capturing WPA/WPA2 Handshake | Cracking Principles [CYBERPUNK ] Capturing WPA/WPA2 Handshake | Cracking Principles [CYBERPUNK ]](https://cdn.cyberpunk.rs/wp-content/uploads/2019/06/Capturing_WPA_WPA2_Handshake_bg.jpg)